Rationale
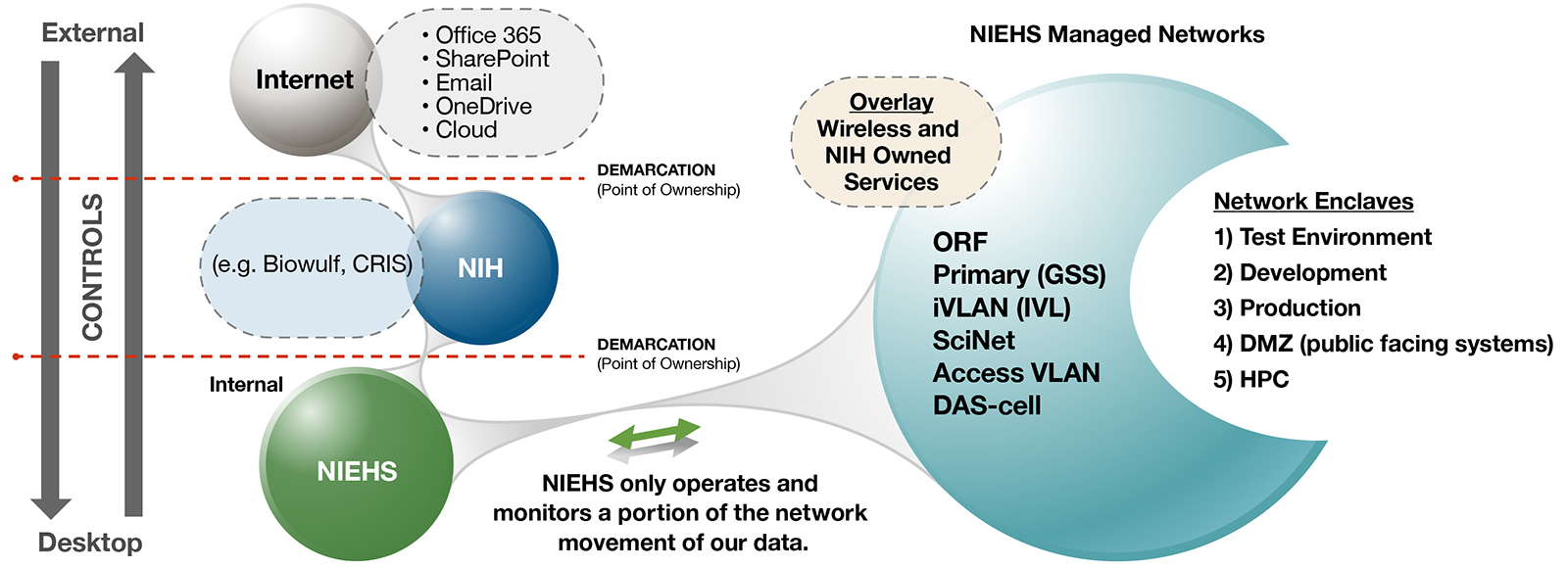
The NIEHS network is made up of many subnetworks. NIEHS operates and controls most, but not all, network components on its campus. The network consists of interconnected devices that provide network access, system distribution, and data center core routing and connectivity for I&IT operations. NIEHS has six locally managed networks and one shared network. On the primary system, the institute hosts five networks, including:
- NIEHSnet (the primary network): NIEHSnet is the general support system (GSS) and commodity network that provides day-to-day network access to the internet and all points in between for NIEHS personnel.
- FACnet (the ORF facilities services network): FACnet is composed of virtual networks that support the Metasys (environmental controls) and Pegasys (physical security) systems. There are several ORF application services on FACnet.
- iVLAN or IVL (a special segment that interconnects laboratory instruments): The instrument VLAN (iVLAN or IVL) is a virtual network that interconnects scientific devices with more I&IT security freedom than the primary network under NIH policy.
- SciNet (a special segment that interconnects some devices to NIH): SciNet is a 10G fiber network used for high-speed data transfers to scientific storage (DDN) and Biowulf.
- Access Control VLAN (a special segment that provides a security layer for new devices on the network): Sometimes called the dungeon, this network functions as an access control step. It functions as a limited access network used to isolate unauthorized users.
NIEHS networks also include two overlay networks referred to as DAS and Wireless. These networks include additional cables, switches, and routers.
- DAS: The interior cellphone signal distribution network allows for individual offices to receive cellphone signals from the primary providers. In 2018, DAS only carried Verizon signals. This limit has critical security and emergency response implications. NIEHS has more than 400 antennas on campus for DAS.
- Wireless: This additional network provides Wi-Fi or wireless computing network. This service is centralized with NIH, but distributed into NIEHS communications rooms. NIEHS sees the wireless network as NIEHS-Wireless and NIH-Guest-Network on devices. The institute modernized the network in 2018 to be compliant with the NIH network modernization project.
Additionally, NIEHS has five network enclaves. Network enclaves are virtual network zones that are logically separated for I&IT security. These networks are often referred to in discussions, but are not always fully delineated in technical layout. Institute enclaves include:
- Test: An environment where application and system developers can create new applications and systems without potentially adversely affecting the commodity network.
- Development: An environment where new systems and applications can be tested in a mock production environment.
- Production: NIEHS GSS and commodity network.
- Demilitarized Zone (DMZ): An environment that is isolated, using security devices, from the commodity network and the internet. DMZ is the NIEHS safety buffer for public-facing systems and devices.
- High-Performance Computing (HPC): NIEHS has isolated a section of the network directed at speed enhancement. The institute operates large and complex servers and storage HPC services.
There are additional descriptive protocols associated with network discussions and services. For example, the new Unified Communications system and its VoIP telephone services are carried by the network. Many network communication protocols are supported by the network. For example, the NIH Active Directory is a form of network communications that makes I&IT devices work. The network refers to many layers and components.
NIEHS Network and Enclave Visualization
The network diagram provides a visual depiction of the complexity of NIEHS virtual networks and enclaves. It shows the ownership of networks, virtual network separation, and network classification. The demarcation marks the point where a network interfaces with the network owned by another entity.
Goals
- Establish a highly flexible, robust, fast, and redundant network that enables the use of new technologies for the NIEHS scientific and administrative community, while employing user access-defined security to prevent breaches, meet HHS mandates, and reduce operational risk.
- Further mature operational enclaves that isolate systems, applications, and databases between NIEHS environments. Enclave definition will increase overall network efficiency and resiliency.
- Implement and respond to continuous monitoring to ensure availability, develop centralized metrics, support planning, and confirm compliance.
- Establish an effective process of network equipment lifecycle, while increasing network capability and reducing overall operational cost.
Strategic Capability Priorities
Network Access Control Deployment
NET-01
NIEHS operates a network access control (NAC) infrastructure that provides security and management controls. This technology is part of an NIH centralization project. NIEHS currently operates end-of-life hardware, so planning for this replacement technology is a priority. The strategy and implementation may require the NIH-required solution with a hybrid local solution. NIEHS purchased CISCO ISE technology in 2018, but also depends on an NIH project to deploy further Forescout technology. Collaborative teams are exploring institute options in the coming months. Success will involve compliant NIH technology working harmoniously with an NIEHS system that reports data to an asset management and security system. Components of this hybrid solution still need to be worked out with NIH.
Network Monitoring Dashboard
NET-02
NIEHS will improve communications with the user community on the status of network operations. The current network dashboard is technical. The desired dashboard will allow all users to receive less technical, but more informative, information about the network as it is impacted. The desired outcome for this objective is an automated and web-enabled dashboard that fits diverse user needs. The project is yet to be prioritized.
Improve Network Monitoring and Reporting
NET-03
NIEHS network performance monitoring is not yet mature. The continued improvement and maturity of the network monitoring capabilities is important to I&IT reliability and integrity. The current data center and server monitoring product, SolarWinds, will be used to monitor the network. The institute will improve and customize this monitoring tool to better support all users. Success measures will involve the creation of custom reports using the tool that monitors specific networks and protocols for performance and consistency, such as VoIP traffic reports, video traffic reports, and facilities network-specific reports. The work is yet to be prioritized.
Optimizing Network Protocols
NET-04
The NIEHS network runs many services and protocols that provide communications for an array of applications. Certain protocols require more bandwidth and control over peak times of communications. Network systems have a quality control implementation called quality of service (QoS) that will be used if there are known gaps in current operations. The tracking, measurement, and reporting of these metrics is needed to determine if the institute requires QoS as a technical capability. NIEHS will add this tracking and reporting to its contracted reports. QoS recommendations will be made for the next one to three years. The project is yet to be prioritized.
Adding Services to the Cellphone Network
NET-05
NIEHS operates and maintains a DAS for cellphone carriers. The DAS improves cellphone reception inside buildings where signals are not normally received. These connections are owned by the providers and the services must be formally arranged. Currently, Verizon is the only operational provider within Building 101. NIH carries all popular providers across the campus DAS, and NIEHS should do the same. The institute will increase its provider network by two carriers over the next two years. Provider expansion is limited by mandated legal agreement review.
Improve Specialized Network Services
NET-06
NIEHS operates secure low-speed DSL network lines supporting several functions. Over time, the number of unrelated uses splitting this internet service has reduced performance. Currently, there are several specialized services using a single DSL line splitting performance for all users. There are several reasons to upgrade the DSL service to a faster connection. Services include on-campus contractors who need high-speed network services, but do not have badges for I&IT systems access; infrastructure services that have cloud-based maintenance monitoring, which are best hosted on a separate network (e.g. Distributed Antenna System); and external monitoring of NIEHS networks. NIEHS will improve network service speed and performance for these purposes by using technology that is faster than DSL for these alternative internet routes. With growth in end-point computing, NIEHS expects expanded needs in this area.
Wireless Network Expansion
NET-07
 NIEHS facilities teams require new wireless services in several campus buildings that do not have wireless service. The project is ORF-funded, and NIEHS is ready to provide new wireless access points when completed. The wireless network will then be added to the NIH wireless network. When the NIEHS facilities team has robust wireless services, the project will be completed. The acquisition is currently moving forward.
NIEHS facilities teams require new wireless services in several campus buildings that do not have wireless service. The project is ORF-funded, and NIEHS is ready to provide new wireless access points when completed. The wireless network will then be added to the NIH wireless network. When the NIEHS facilities team has robust wireless services, the project will be completed. The acquisition is currently moving forward.
IPv6 Planning With NIH
NET-08
The federal government is required to deploy native Internet Protocol version 6 (IPv6) network protocols to public-facing I&IT services. The new technology requires an internal network strategy and plan for transition. NIEHS will produce a documented plan that details the strategy and considers timing and options for this project. NIH has not required additional action, even though the prescribed timeline has passed.
Develop Out-of-Band Network for I&IT Management
NET-09
NIEHS needs an out-of-band (OOB) network to improve the ability to operate and maintain the network. An OOB network will provide a separate connection to certain devices for direct management that does not depend on the operating systems of the primary network. OOB systems use a dedicated network that is up all the time. As an initial strategy, NIEHS will use retired lifecycle equipment to minimize OOB cost and complexity. An OOB network governing strategy will be generated. OOB planning has been initiated, but not prioritized.
Network Theme Map
| I&IT Landscape | Agility | Analytics | Communications & Transparency | Foster Collaboration | Governance | Optimize Resources | Workforce Development |
|---|---|---|---|---|---|---|---|
| Network | NET-07 NET-08 NET-09 | NET-01 NET-03 NET-04 | NET-02 | NET-05 | NET-06 |
See Appendix A: I&IT Priorities Support NIEHS Strategic Themes


